Monitoring Security Vulnerabilities in Your Cloud Vendors
Introduction
If you manage applications running on cloud platforms, you likely depend on multiple cloud vendors and services. These could be infrastructure providers like AWS, GCP or Azure. A vulnerability in any of these services could potentially impact your applications and your users.
A cloud platform has many moving parts, many of which are dependent on other third-party providers. For example:
- Operating system images for VMs which are maintained by third-party vendors.
- Container images which are hosted on external repositories.
- Software stacks which are maintained by other vendors but available for deployment on the cloud provider.
- Libraries used by the cloud provider's internal software which are maintained by other developers or organizations.
- Control plane software like Kubernetes.
- Hardware, like processors, which are provided by the manufacturer.
- Hypervisors which are developed and maintained by third-party vendors.
- Networking hardware manufactured by other vendors.

- Introduction
- Why Monitoring Cloud Vendors' Security is Important
- How To Stay Updated About Cloud Vendor Security Issues
- Tools and Services to Monitor Cloud Vendor Security
- Best Practices
- Conclusion
This guide is particularly relevant for:
- Ops/SRE folks managing cloud applications on cloud platforms.
- Security teams responsible for application security.
- Engineering managers and VPs overseeing cloud operations.
It is important to distinguish between the security issues affecting the cloud vendor's services and the issues affecting the applications running on the cloud. The cloud vendor is responsible for the security of its infrastructure, including:
- Mitigating vulnerabilities in its control, including datacenter, network, hardware and control plane software.
- Making patches available for third-party hardware and software that are part of its platform once they are provided by the third-parties. E.g hypervisors, processors, VM images.
The cloud vendor is not responsible for the security of the application code that users run on it. As a cloud user, you are responsible for that.
However, your responsibility as a cloud user also includes:
- Staying abreast of security vulnerabilities in the cloud vendor's infrastructure.
- Updating your applications to use the latest versions of the libraries and frameworks that you depend on.
- Updating to the latest and secure versions of the software stacks that you use but are provided by the cloud vendor. E.g. VM images, Kubernetes versions, etc.
We will cover the how to stay on top of security vulnerabilities in the cloud vendor's infrastructure in this article.
Why Monitoring Cloud Vendors' Security is Important
Security Risks in Cloud Services
Cloud vendors face security challenges that could impact your applications:
-
Infrastructure Vulnerabilities
- Zero-day exploits in hypervisors.
- Vulnerabilities in container runtimes.
- Network protocol weaknesses.
- Hardware-level security flaws.
-
Software Supply Chain Issues
- Compromised dependencies being used by the cloud vendor's software.
- Outdated and vulnerable third-party libraries.
- Malicious container images.
-
Configuration Risks
- Default settings that may be insecure.
- Misconfigurations in service integrations, especially when services are developed by different vendors.
- Access control weaknesses.
- Gaps in API security.
- Expired certificates.
-
Compliance and Regulatory Risks
- Data privacy violations.
- Regulatory non-compliance.
- Geographic data residency issues.
- Certification lapses.
Although Compliance and Regulatory issues are an important part of security, we will not cover them in this article because they are not directly related to the building blocks of the cloud vendor's infrastructure.
The impact of these vulnerabilities can be severe:
- Data breaches exposing sensitive customer and company information.
- Service disruptions affecting SLAs.
- Financial losses from security incidents.
- Damage to company reputation.
- Legal and regulatory consequences.
Real-World Examples
Some recent incidents highlight the importance of monitoring cloud vendor security:
- Meltdown CPU vulnerability (2018).
- Spectre CPU vulnerability (2017).
- Solarwinds supply chain attack (2019-2020).
- Azure Cosmos DB vulnerability (2021).
How To Stay Updated About Cloud Vendor Security Issues
Cloud vendors publish security advisories on their websites. These advisories are published in the form of blog posts, emails, and sometimes in the form of security bulletins. You can subscribe to these advisories to stay updated. You might also want to monitor vulnerabilities in the software stacks that you use. E.g. Kubernetes, Docker, etc. Even if you use managed versions of these, you can get to know about security issues before your cloud vendor reports it and releases an updated version of the stack.
Links to Some Cloud Vendor Security Advisories
- AWS Security Bulletins
- Azure Security Advisories
- Google Cloud Security Bulletins
- Oracle Cloud Security Advisories
- IBM Cloud Security Advisories
- Red Hat Cloud Security Advisories
- Cisco Security Advisories
- Broadcom VMware Cloud Security Advisories
- Dell Security Advisories
- TencentCloud Security Advisories
- Fastly Security Advisories
These links are valid as of this writing (December 2024).
Based on the publicly available data in the above links, we can see trends in different cloud vendors' security advisories.
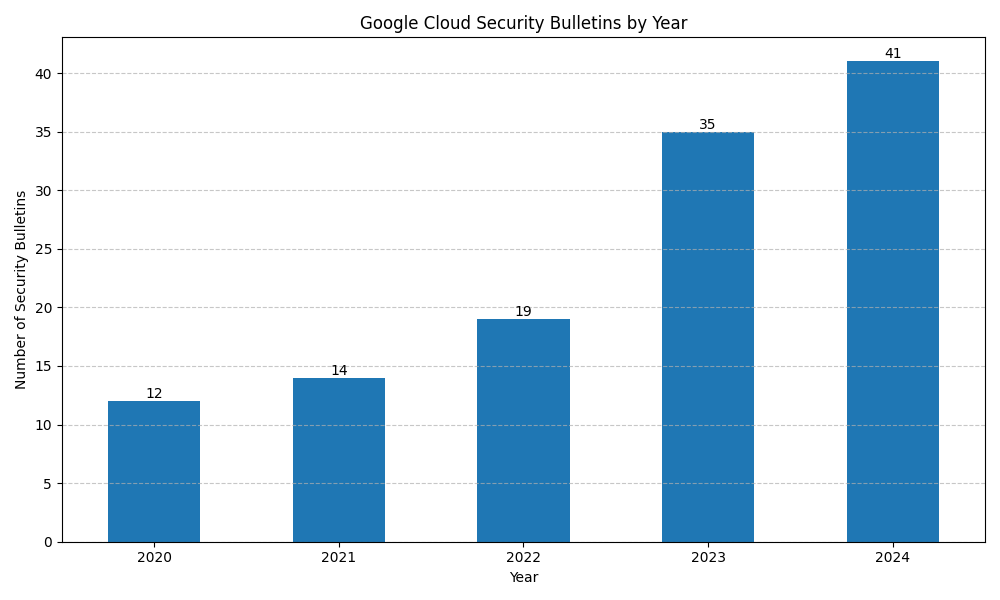
Source: Generated from the Google Cloud Security Bulletins page data.
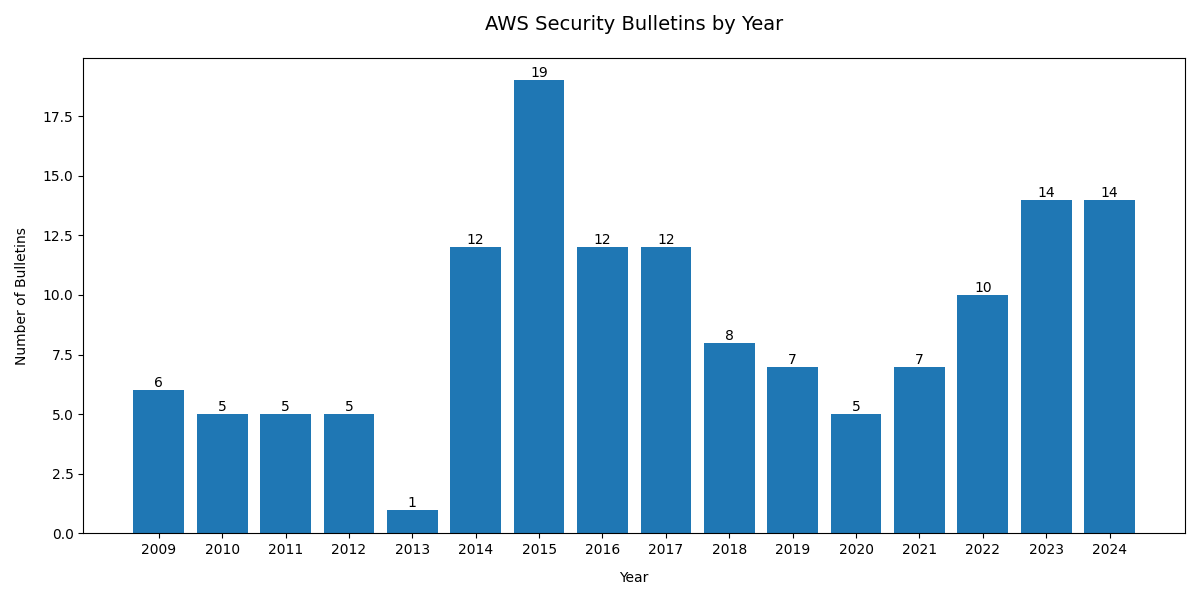
Source: Generated from the AWS Security Bulletins page data.
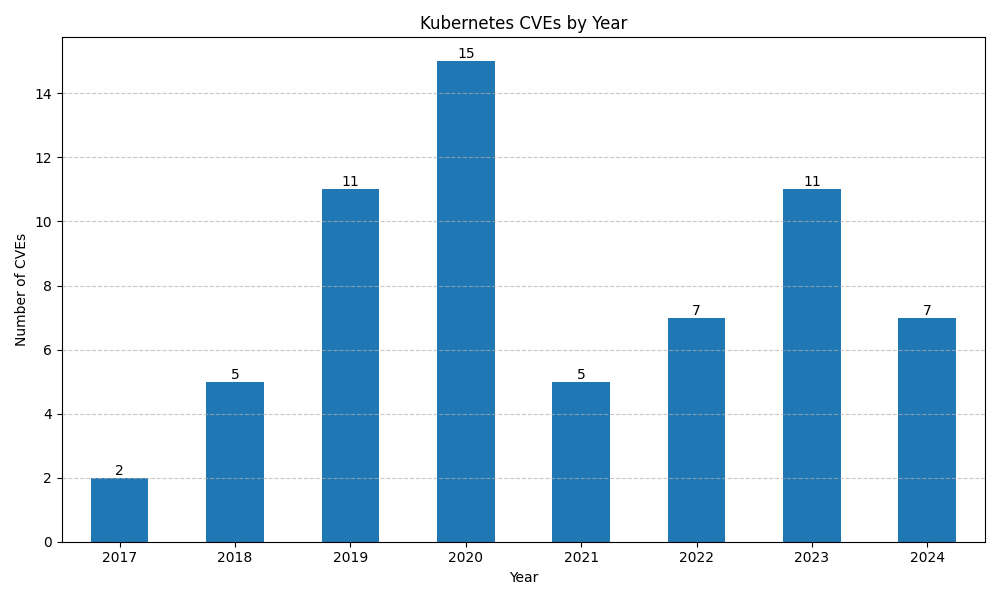
Source: Generated from the Kubernetes Security Bulletins page data.
Note that there are multiple factors that affect the advisory count, and a rising trend does not necessarily mean that the cloud vendor is not doing a good job.
- The number of vulnerabilities in dependent software.
- The number of vulnerabilities in dependent hardware.
- The number of vulnerabilities actually discovered.
Tools and Services to Monitor Cloud Vendor Security
When it comes to staying updated, there are different approaches. Choose the one that works for you.
RSS Feeds
If the bulletin page has the option of subscribing to RSS feeds, you can use that to get updates. You can tie in the RSS feed to your email client or Slack channel.
Email Alerts
If the bulletin page has the option of subscribing to email alerts, you can use that to get updates.
Cloud Dashboard Alerts
If your cloud vendor has the option of sending you security notifications in your dashboard, you can use that. However, this has the drawback that you won't see the alert unless you are signed in and monitoring your dashboard.
Best Practices
- Do periodic reviews of which security advisories you are monitoring. Your team(s) might have started using a new cloud vendor or dropped an existing one.
- If mitigation requires a migration - e.g. to new VMs, or a new version, track it like any other development task. This is especially important if you have many applications or a distributed architecture.
- When a security advisory is published, identify potential attack vectors in your applications and if possible test for them. You might have to take alternative measures until the vendor releases a patch.
- Maintain communication with stakeholders throughout the process.
Conclusion
Keeping track of your cloud vendors' security updates and vulnerabilities is important to your business. It helps you ensure that your applications are not exposed to risk.
Image credits: Photo by Pawel Czerwinski on Unsplash

