The IncidentHub Blog
This is the official blog of IncidentHub - the status page aggregator.
How to Monitor SaaS Status in 2026 : A Complete Guide

Major Cloud Outages of 2025

How to Receive Cloud Outage Alerts in Microsoft Teams
Product Update - Turn Off Alerts, Use Microsoft Teams, and Custom Domains
The 2025 Guide to Open Source Status Page Software

Improving the Developer Experience by Monitoring Third-Party Outages

The Ultimate Guide to Incident Management Tools in 2025

Mistakes To Avoid With Your Public Status Page
Best Practices for Planning for Upcoming Cloud Maintenance
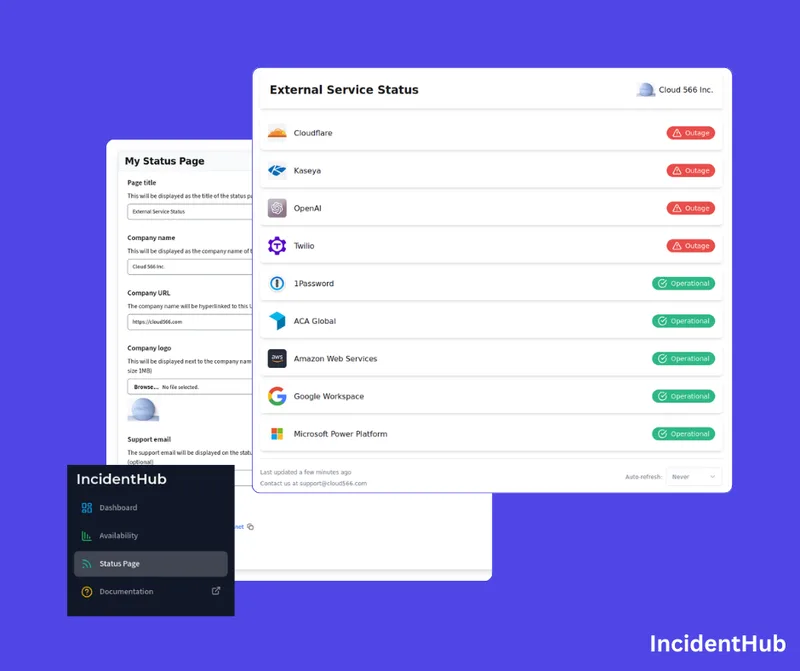
Product Update - Public Status Pages
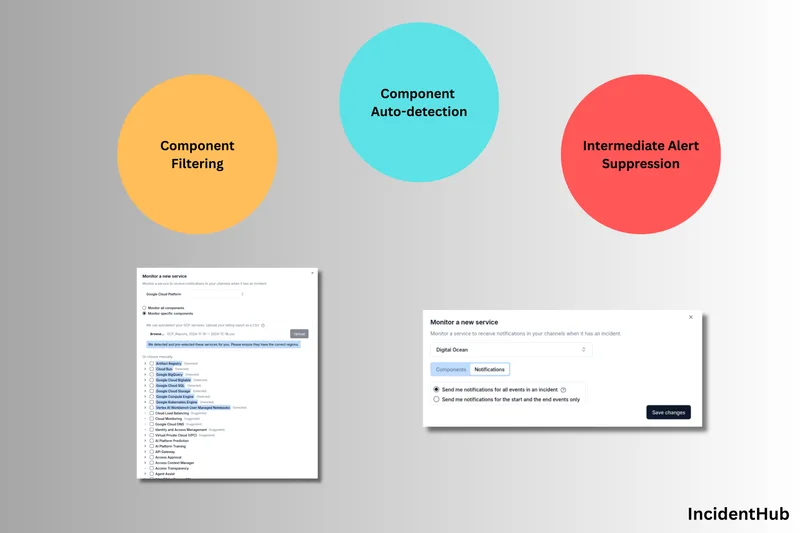
How to Fine Tune Your IncidentHub Alerts
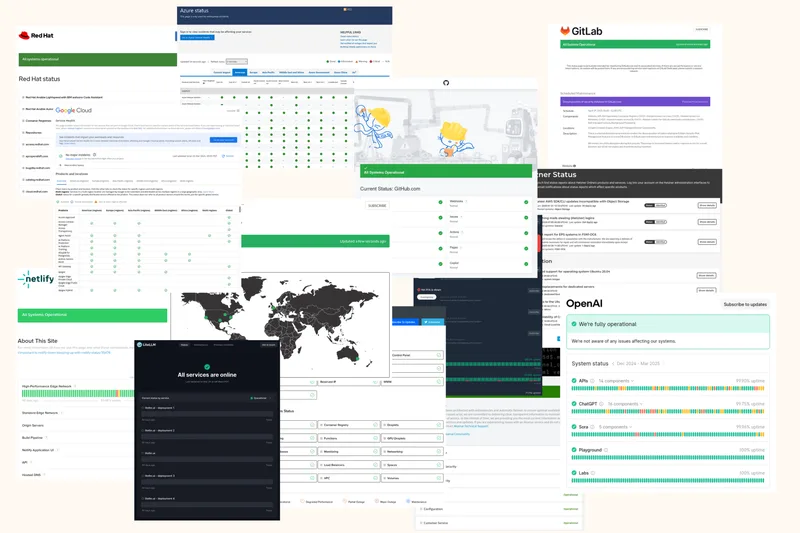
Top 6 Reasons Why You Need a Status Page Aggregator

How to Receive IncidentHub Alerts in your Webhook
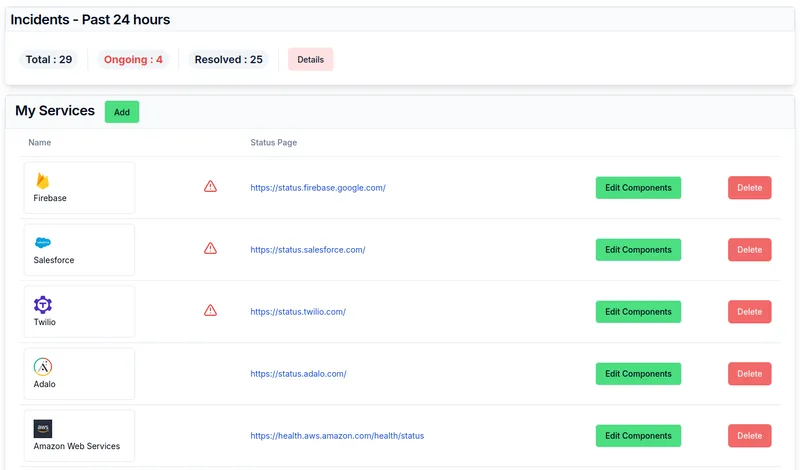
January 2025 Product Update - Easier Onboarding, Better User Experience, and Reliability Improvements